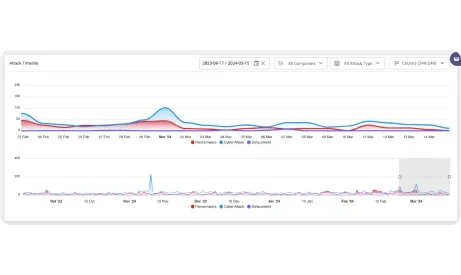
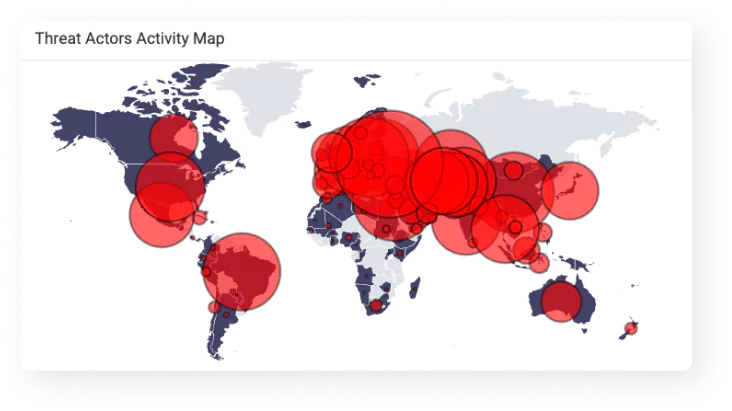
Experience a new era of cyber protection with SOCRadar’s high-octane Cyber Threat Intelligence Module. Leveraging the power of big data, we transform your cybersecurity operations, delivering lightning-fast, real-time threat insights and deep-dive context analysis.
Strengthen your business’s digital frontier with Dark Web Radar. This cutting-edge tool arms your enterprise with a trio of digital superpowers: vigilant Dark Web Monitoring, robust Fraud Protection, and an insightful Dark Web Search Engine. Transform into a proactive warrior against hidden cyber dangers.
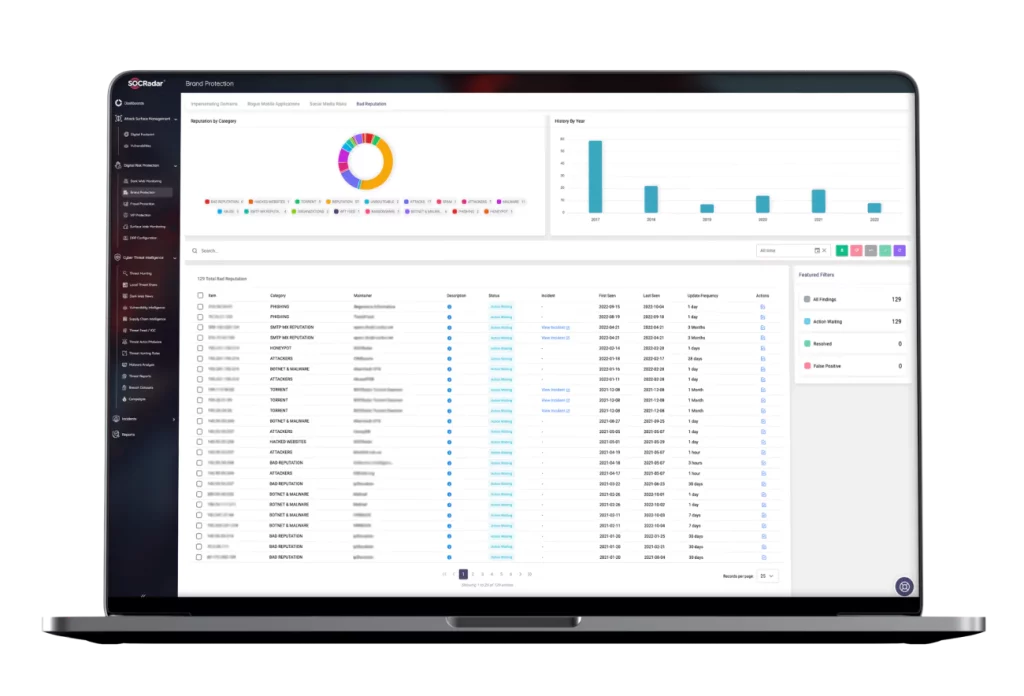
SOCRadar’s Brand Protection Service is power-packed with advanced phishing detection, comprehensive internet scanning, and robust compromised credential detection, and it makes massive data meaningful with precise, actionable alerts.
Track your digital assets in real-time, sharpening your understanding of your attack surface and guarding them like a pro. With our pioneering continuous monitoring algorithms, we illuminate your digital landscape, forecasting future risks with no manual inventory required. With EASM, cybersecurity becomes effortless and efficient.
Gain crystal-clear visibility into your entire supply chain with SOCRadar Supply Chain Intelligence. SOCRadar empowers informed decision-making by providing rich insights on over 50 million companies across hundreds of sectors and 249 countries. Access a wealth of detailed information, including the latest cybersecurity news, 3rd Party Assessment Reports, popularity rankings, and cyber exposure levels.