Adopt a CTEM approach and 2x your ability to prevent attacks.

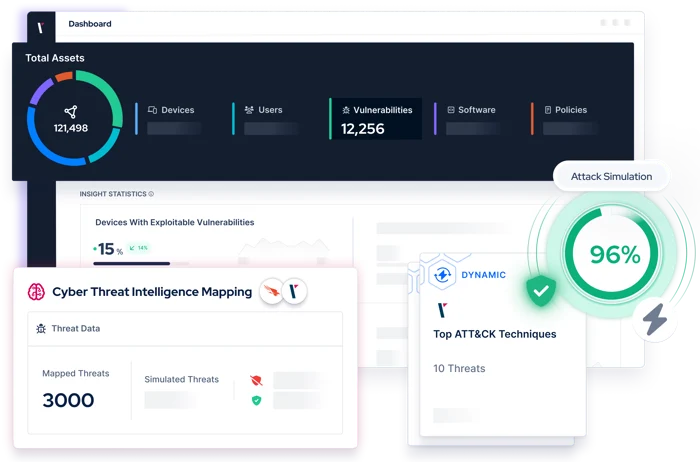
Determining which threats and vulnerabilities to prioritize is a challenge every security team faces.
Continuous Threat Exposure Management (CTEM) is a holistic approach to cybersecurity that helps security teams focus on the exposures that will impact risk reduction most effectively. It is one of Gartner’s Top Strategic Technology trends this year.
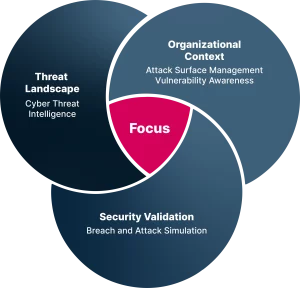
Siloed approaches make it difficult to manage your threat exposure successfully.
In a single platform, Picus supplies the context you need to make better security decisions across all areas of your security program.
Security validation insights, combined with data from the threat landscape and your attack surface, enable you to focus remediation and mitigation in the areas that matter.
Get the capabilities you need to adopt a Continuous Threat Exposure Management approach.
Get a consolidated and up-to-date view of your internal and external assets and understand the risks they pose.
By integrating asset and vulnerability data, identify which assets are at risk based on their profile and whether endpoint security controls are in place to provide protection.
Consistently measure the effectiveness of your security controls with accurate attack simulations.
Understand if your prevention and detection controls are configured to provide the coverage and visibility you need to protect your assets against the latest threats.
Obtain the context you need to prioritize gaps and vulnerabilities.
By combining asset, vulnerability, and validation insights, determine which exposures pose the most significant risk and which actions will have the greatest impact on addressing them.
Receive actionable mitigation insights to address any exposures identified, such as misconfigured network settings, policies and security controls.
Vendor-specific prevention and detection content for network and endpoint security controls empowers you to optimize your capabilities swiftly, and reduces the manual effort required.
Keeping pace with the rapidly changing threat landscape is tough – there are always new threats to respond to and vulnerabilities to patch.
By validating the effectiveness of your controls and process with attack simulation, Picus helps you understand which threats pose the greatest risk and take action to mitigate any exposures they are likely to exploit.
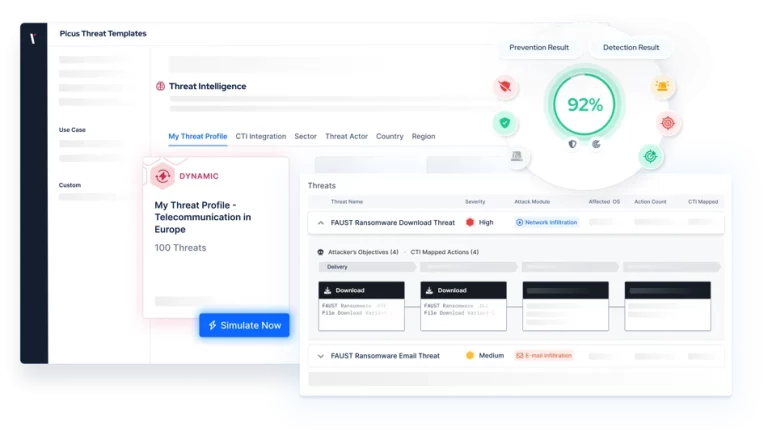
Address Challenges with Security Validation
See and prioritize exposures across your security operations.